Introduction: Protecting Your Business in a High-Stakes Marketplace
Every quarter, eBay processes over $2.3 billion in transactions, making it a powerhouse of global e-commerce. But behind this staggering number lies a hidden risk for sellers: multi-million dollar businesses have been destroyed because eBay’s algorithms detected “suspicious patterns” that were actually just good business practices. This is where a stealth eBay account becomes not a tool for deception, but a crucial strategy for survival.
The concept of a "stealth account" is fundamentally about business protection. It involves creating and managing multiple, independent eBay accounts in a way that prevents them from being linked by eBay's aggressive and often flawed detection systems. This article provides a comprehensive guide for serious sellers on how to make successful stealth ebay account identity. The goal is not to game the system, but to build sustainable, protected income streams that can withstand the platform's volatility and secure your financial future.
Why Every Serious eBay Seller Needs a Stealth Account Strategy
Moving beyond the fear of a sudden ban, using multiple accounts is a sound business strategy. For ambitious sellers, diversification is key to growth, stability, and risk management. However, eBay actively works to connect accounts that it believes belong to a single user, creating a significant operational challenge that must be overcome with a professional security protocol.
The core problem is account linking. eBay uses sophisticated browser fingerprinting and other surveillance techniques to identify relationships between accounts. If a link is found, all associated accounts can be suspended simultaneously, even if only one was flagged for a minor infraction. This makes a stealth strategy essential for any seller looking to scale their operations securely, including learning how to make successful stealth ebay account identity.
Legitimate Reasons for Multiple eBay Accounts
- Product Diversification: Selling different product lines under unique and separate brand identities.
- Geographic Expansion: Targeting different international markets with localized storefronts and strategies.
- Risk Management: Insulating your main business from platform risk by operating backup accounts.
- Business Scaling: Managing high sales volume more effectively across multiple, specialized stores.
- Family Business: Allowing multiple family members to run their own distinct businesses from a shared location.
The Severe Consequences of Detection
When eBay links your accounts, the fallout can be catastrophic for your business:
- Immediate suspension of all connected accounts.
- Loss of access to funds held in your accounts.
- A permanent ban prevents you from creating new accounts.
- Potential legal action for policy violations.
To build an unbreakable defense, you must first become an expert in the weapons used against you, including learning how to make successful stealth ebay account identity.
Deconstructing eBay's Detection Methods for Learning How to Make Successful Stealth eBay Account Identity
To build an unbreakable defense, you must first become an expert in the weapons used against you. This section dissects eBay's surveillance arsenal, piece by piece, so you can neutralize every threat. eBay's methods are sophisticated and multi-layered, analyzing everything from your hardware to your listing habits.
Digital Fingerprinting
This is the process of collecting unique information about your browser and computer settings to create a distinct "fingerprint." Even without cookies, eBay can identify your device with remarkable accuracy by analyzing:
- Browser type and version
- Screen resolution and color depth
- Installed fonts and plugins
- Time zone and language settings
- Hardware specifications (Canvas, WebGL, Audio context)
Network Analysis
eBay closely monitors how you connect to its platform to identify shared networks, which are a major red flag for linked accounts. This includes tracking:
- IP addresses and their geolocation
- Proxy detection algorithms that flag low-quality or datacenter IPs
- Network routing patterns
Behavioral Patterns
Your actions on the site create a pattern that algorithms can analyze. eBay's systems look for similarities in user activity that suggest a single person is operating multiple accounts, such as:
- Listing patterns and the timing of new posts
- Pricing strategies
- Communication styles used in customer messages
- Login times and the frequency of activity
Payment and Shipping Connections
The most straightforward way accounts are linked is through shared logistical and financial information. These are hard data points that are difficult to dispute:
- Bank accounts and credit cards
- PayPal accounts
- Shipping and return addresses
- Phone numbers
Now that you understand the threats, it's time to construct the operational security infrastructure required to defeat them and learn how to make successful stealth ebay account identity.
Building Your Stealth eBay Account Infrastructure for Success
A successful stealth eBay account is built on a solid foundation of the right tools and strategies. This foundation rests on three pillars: creating separate digital identities, managing your IP addresses, and ensuring device separation. With this foundation meticulously constructed, you are no longer a target but an operator.
Separate Digital Identities
Each of your eBay accounts must appear to be a completely different person using a different computer. An antidetect browser is the essential tool for achieving this. This directly counters eBay's Digital Fingerprinting by ensuring that each account's unique signature (Canvas, WebGL, fonts) is completely isolated.
DICloak provides the necessary features to create these isolated identities:
- Unique browser fingerprints for each account.
- Separate cookie and session storage to prevent data leaks.
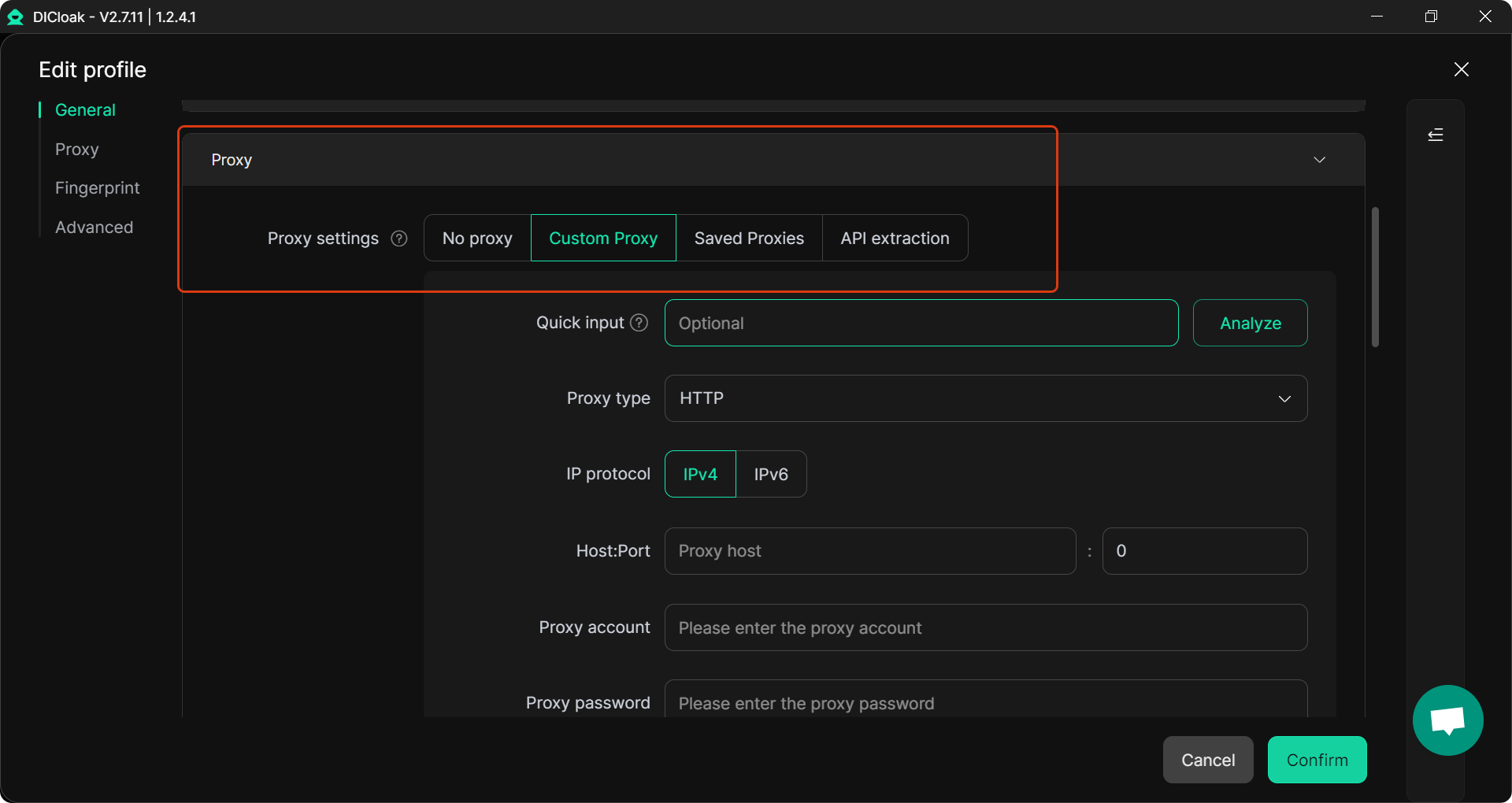
- Custom proxy configuration.
- Isolated browsing profiles.
IP Address Management
Using the same IP address for multiple accounts is a critical error that is easily flagged by eBay's Network Analysis. Proper IP management is non-negotiable and requires the following:
- Use clean residential proxies from different geographic locations.
- Maintain a consistent IP for each specific account to mimic normal user behavior.
- Avoid IPs with a history of eBay violations or those on public blacklists.
Device Separation
Beyond the browser fingerprint, each account should appear to originate from a different physical device. An antidetect browser helps create this illusion by allowing you to control and vary key hardware and software parameters for each profile. Factors that contribute to this separation include:
- Different operating systems (e.g., Windows, macOS).
- Various screen resolutions.
- Separate device emulation profiles.
With this infrastructure in place, you are now prepared to execute the precise, multi-phase process of bringing your first stealth account to life and understanding how to make successful stealth ebay account identity.
A Step-by-Step Guide to Creating a Stealth eBay Account and Maintaining Identity
This section provides a clear, phased roadmap for creating a durable stealth account. Rushing this process is the fastest way to get detected. Patience and meticulous attention to detail are your greatest assets, ensuring each step is completed carefully before moving on to the next.
Phase 1: Preparation
- Set Up Your Infrastructure: Install DICloak, acquire high-quality residential proxies, and prepare separate, aged email addresses, unique phone numbers, and distinct payment methods for each account you plan to create.
- Create Unique Identities: Develop a complete and distinct seller persona for each account. This includes a different business name, a specific product niche, unique branding elements, and a clear target market.
Phase 2: Account Creation and Warming
- Technical Setup: In DICloak, create a new browser profile. Configure its digital fingerprint to be unique, ensuring it aligns with the device and location you want to emulate. Connect this profile to one of your clean residential proxies.
- Clear Data: Clear all cookies and browsing data before navigating to eBay.
- Account Registration: Use your prepared information—the aged email, a unique username, and consistent personal details—to register the new account on eBay. Complete the phone verification immediately.
- Payment Setup: Set up a PayPal account using information that matches your new seller persona.
- Initial Account Warming: For the first several days, do not list any items. Use the account only for browsing products and making a few small purchases. Leave positive feedback as a buyer to build an initial layer of trust and activity history.
Phase 3: Developing the Seller Account
- Listing Strategy: Start by listing a few low-value, low-risk items. It is crucial to use unique product photos (never stock images), different listing descriptions, and varied pricing. Avoid copying any details from your other accounts.
- Building Reputation: Focus on providing excellent customer service and shipping items quickly to build positive feedback. As eBay raises your selling limits, you can gradually and naturally increase the number and value of your listings.
Mastering this foundational process is the prerequisite for implementing the advanced operational security needed for long-term growth, and learning how to make successful stealth ebay account identity is key to ensuring success.
Common Mistakes That Lead to Detection in How to Make Successful Stealth eBay Account Identity
Even with a professional setup, simple operational errors can compromise your entire network of accounts. Avoiding these common mistakes is just as important as having the right tools. This section serves as a critical checklist of what not to do.
Technical Errors
- Browser Fingerprint Overlap: Using similar browser or device configurations across different accounts, which allows algorithms to spot a pattern. This is a key reason how to make successful stealth ebay account identity can fail.
- IP Address Reuse: Accidentally logging into one account using an IP address designated for another. This is a crucial mistake when learning how to make successful stealth ebay account identity.
- Cookie Contamination: Failing to use completely isolated browser sessions, allowing tracking cookies from one account to "leak" into another. This can undermine efforts to create a stealth identity.
- Using Low-Quality Proxies: Employing datacenter or blacklisted proxies that are easily flagged by eBay’s detection systems. Using the wrong proxies is a critical error when trying to establish how to make a successful stealth ebay account identity.
Behavioral Patterns
- Copying Product Descriptions: Reusing titles, descriptions, or even parts of descriptions across different accounts. This can be a red flag when trying to build a successful stealth ebay account identity.
- Listing at the Same Times: Creating new listings or ending auctions at identical times, suggesting an automated or single-user operation. This is one of the behaviors you must avoid when learning how to make a successful stealth ebay account identity.
- Using Identical Store Policies: Copying and pasting return policies, shipping terms, or other business information. This can cause account links and disrupt efforts to maintain a stealth identity.
- Having a Uniform Communication Style: Responding to customer inquiries with the same tone, phrasing, or templates. To protect how to make successful stealth ebay account identity, you must ensure every account has a unique communication style.
Business Connections
- Sharing Payment Methods: Using the same bank account, credit card, or PayPal account for more than one eBay store. This is a major mistake that violates how to make successful stealth ebay account identity strategies.
- Using Similar Addresses: Listing shipping or return addresses that are geographically too close or have similar formatting. This undermines your effort to maintain separate identities for each account.
- Reusing Phone Numbers: Linking more than one account to the same phone number for verification or contact purposes. To truly understand how to make successful stealth ebay account identity, avoid this mistake.
- Sourcing from Identical Suppliers: Creating logistical patterns by having identical products shipped from the same supplier addresses. This is a mistake that can break how to make successful stealth ebay account identity.
By vigilantly avoiding these errors, you can transition from basic account creation to proactive management required for long-term health and growth, while mastering how to make successful stealth ebay account identity.
Maintaining Long-Term Health and Scaling Your Stealth eBay Account Identity
Creating a stealth account is only the beginning. The real work lies in maintaining its security over time and safely scaling your operation. This section provides expert strategies for long-term management, helping you protect your assets as your business grows.
Regular Security Audits
Conduct monthly checks on your infrastructure and accounts to ensure everything remains secure and separate. Key audit points include:
- Proxy Performance: Check that your IPs are clean and not on any blacklists. Maintaining how to make successful stealth ebay account identity starts with using high-quality proxies.
- Browser Fingerprint Uniqueness: Verify that your browser profiles in DICloak remain distinct and have not been compromised. This ensures that each account's identity remains isolated, a critical part of how to make successful stealth ebay account identity.
- Account Performance Metrics: Monitor your seller ratings to stay ahead of any potential issues that could draw unwanted attention. This is especially important for the ongoing health of your how to make successful stealth ebay account identity.
Scaling Considerations
When you are ready to add new accounts to your portfolio, follow these best practices to minimize risk:
- Space out new account creations by several weeks. This helps in maintaining separate identities and learning how to make successful stealth ebay account identity effectively.
- Use completely different infrastructure for each new account. This is critical to building and maintaining how to make successful stealth ebay account identity over time.
- Develop distinct business models and operational procedures to avoid creating any patterns that could jeopardize how to make successful stealth ebay account identity.
Risk Management Strategies
Protect your business financially and operationally by diversifying your assets and minimizing your exposure to any single account.
- Account Diversification:
- Spread inventory across multiple accounts and different product categories.
- Target various customer segments.
- Maintain separate supplier relationships. These practices are essential for protecting how to make successful stealth ebay account identity.
- Financial Protection:
- Use separate business bank accounts and PayPal accounts for each storefront to isolate your finances. This ensures that you do not jeopardize how to make successful stealth ebay account identity by mixing finances.
- Keep minimal funds in any single account by regularly withdrawing earnings. This minimizes risk and helps preserve how to make successful stealth ebay account identity.
Managing this complexity manually is prone to error, which is why a professional tool like DICloak becomes indispensable for scaling sellers and mastering how to make successful stealth ebay account identity.
How to Use DICloak to Protect Your Stealth eBay Account Identity
For professional eBay sellers who need to manage multiple accounts, DICloak provides a comprehensive solution that combines security, efficiency, and scalability. It is designed to handle the complexities of maintaining separate digital identities, allowing you to focus on growing your business instead of worrying about detection. Mastering how to make successful stealth ebay account identity is easier with the right tools in place.
Here are the key benefits of using DICloak for your eBay operations:
- Complete Account Isolation: Each account benefits from independent session management and isolated local storage, leaving no digital breadcrumbs for eBay to follow. DICloak gives each eBay account its own unique browser fingerprint, making them appear as if they are run by different people on separate computers. This is essential for mastering how to make successful stealth ebay account identity.

- Custom Proxy Configuration: DICloak allows you to integrate your own proxies, helping maintain the integrity of how to make successful stealth ebay account identity.
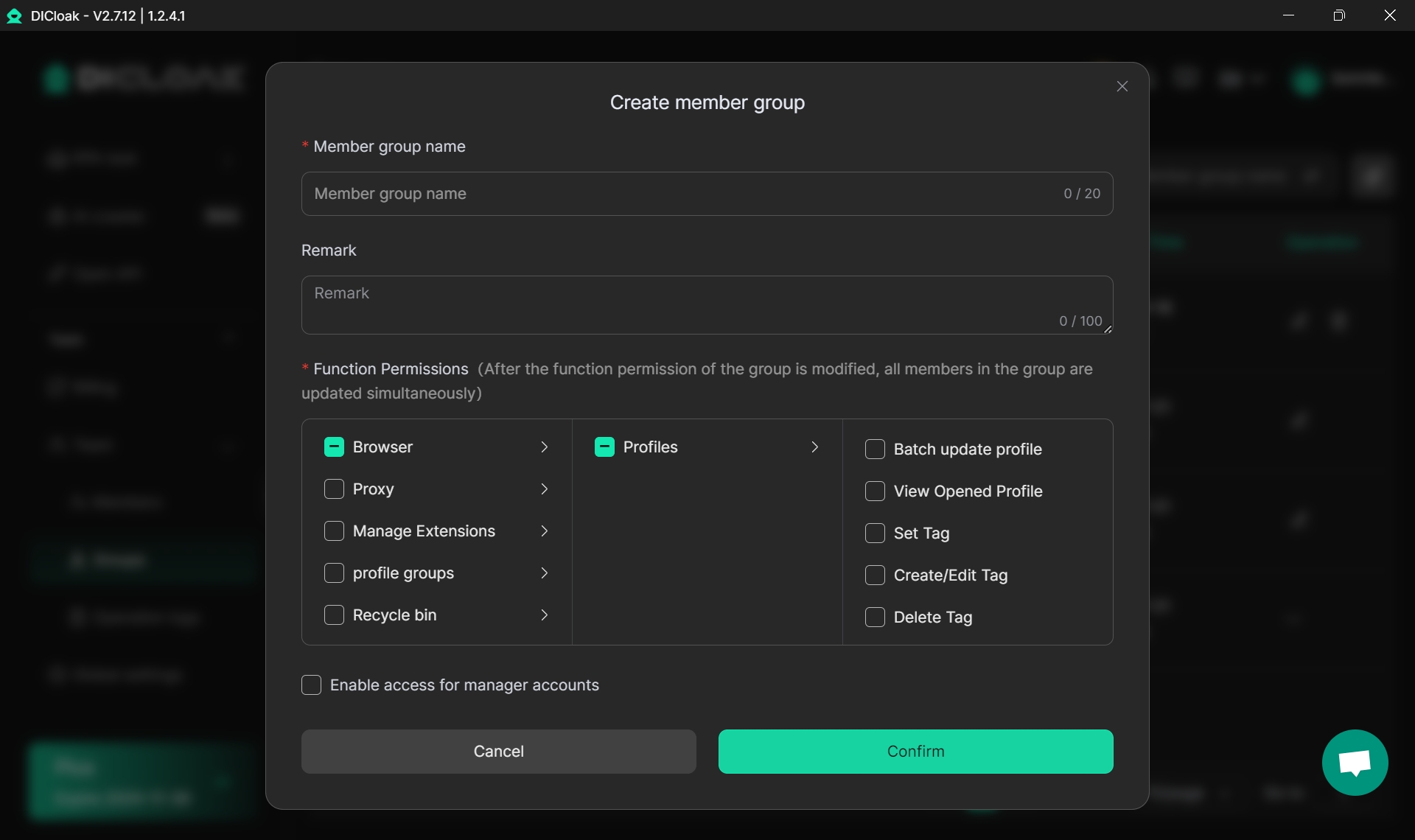
- Team Collaboration Features: As your business grows, you can securely share browser profiles with team members, manage their access levels, and oversee all account activity without compromising security. This makes how to make successful stealth ebay account identity scalable and collaborative.
With the right operational security tools in place, it is vital to address the broader context of running this type of operation responsibly.
Legal and Ethical Considerations in Creating a Successful Stealth eBay Account Identity
It is natural to have questions about the legitimacy of operating stealth accounts. When executed correctly and for the right reasons, this strategy is about responsible business management and risk mitigation, not deception. Building trust starts with operating each account ethically and professionally, which is key to how to make successful stealth ebay account identity.
- Staying Within eBay’s Terms: While you are separating your accounts, each individual account must still adhere to all of eBay's policies. This means providing accurate information, following all seller rules, and representing a distinct business operation. This is essential when learning how to make successful stealth ebay account identity.
- Business Legitimacy: Treat each stealth account as a real, standalone business. This includes managing separate inventory, providing dedicated customer service, and maintaining independent financial records. The goal is operational separation, not just technical masking, which is crucial for how to make successful stealth ebay account identity.
- Tax and Legal Compliance: You are fully responsible for the legal and financial obligations of your businesses. This includes reporting all income from every account to the relevant tax authorities and complying with all local and national business regulations. Treating each account as a separate business entity is a key part of how to make a successful stealth ebay account identity.
The key is treating each account as a separate, legitimate business with its own identity, operations, and customer base. By doing so, you can build a resilient and diversified e-commerce portfolio. Using professional tools like DICloak is the key to executing this strategy safely, effectively, and at scale, ensuring that how to make successful stealth ebay account identity is maintained across multiple accounts.
Frequently Asked Questions (FAQs)
Is it legal to create stealth eBay accounts?
Creating multiple eBay accounts isn’t illegal, but it must be done in compliance with eBay’s terms of service. Each account should represent a legitimate, separate business operation with distinct inventory, suppliers, and operations. Learning how to make successful stealth ebay account identity means ensuring your accounts comply with these regulations.
How many eBay accounts can I manage safely?
There is no set limit to the number of accounts you can manage. Success depends entirely on your ability to maintain complete operational, technical, and behavioral separation for each one. It is best to start small with 2-3 accounts and scale slowly as you perfect how to make successful stealth ebay account identity.
What happens if eBay discovers my stealth accounts are linked?
If eBay’s systems link your accounts, they may suspend all of them simultaneously, even the ones with perfect performance records. This is why using professional tools for fingerprint and IP management is essential to prevent detection and protect how to make successful stealth ebay account identity.
Can I sell the same products on different stealth accounts?
It’s risky to sell identical products across accounts, as this can trigger eBay’s detection systems. Focus on different product categories, suppliers, or target markets for each account to maintain separation and ensure how to make successful stealth ebay account identity remains intact.
How much time should I leave between creating new eBay accounts?
To minimize risk, you should wait at least 2-4 weeks between creating new accounts. It is also critical to use completely different and new infrastructure (proxies, emails, payment methods) for each new account to avoid creating any links, ensuring how to make successful stealth ebay account identity is not compromised.