Have you ever wanted to browse the internet without revealing your real IP address? Or maybe you've faced restrictions on accessing certain websites based on your location? Whether you are looking to protect your privacy, avoid tracking, or bypass geographical limits, a proxy browser might be the perfect solution.
A proxy browser works by acting as an intermediary between you and the websites you visit. It hides your actual IP address, replacing it with a different one from a proxy server. This process helps keep your online activity anonymous and secure, providing a shield against surveillance and potential cyber threats. It's especially useful for users who need to maintain privacy while managing sensitive data or bypassing location-based restrictions.
In this article, we will explore the core functions of a proxy browser, its benefits, and how it works to safeguard your online presence. Get ready to discover how this tool can enhance your browsing experience and provide you with the ultimate protection from unwanted tracking!
What is a Proxy Browser?
A proxy browser is a specialized web browser that routes your internet traffic through a proxy server, rather than directly connecting to the websites you visit. This method helps hide your real IP address, improving your privacy and online security.
Key Functions of a Proxy Browser:
- Hiding Real IP Address: By using a proxy server, the website can only see the proxy server's IP address, not your real one, which helps protect your identity.
- Bypassing Geo-restrictions: Proxy browsers allow you to access websites that are restricted based on your location by choosing a proxy server from a different region.
- Enhanced Security: They can also protect you from malicious websites and reduce the risk of data breaches.
Cybersecurity and Proxy Browsers
1.Types of Proxy Browsers
Proxy browsers come in various forms, each serving different purposes. Understanding these types is crucial for recognizing potential threats.
- Anonymous Proxy Browsers: These hide the user's real IP address but still identify themselves as proxies. They're commonly used for general privacy protection.

- Rotating Proxy Browsers: These frequently change IP addresses, making it challenging to detect and block malicious activities. They're often used in web scraping and automated attacks.
- Mobile Proxy Browsers: Utilizing real mobile devices and networks, these proxies mimic legitimate mobile user behavior, complicating detection efforts.

- Browser-Based Proxy Extensions: These are lightweight tools integrated into browsers, allowing users to route traffic through proxies easily. While convenient, they can be exploited for malicious purposes.
2.Detection Challenges
Detecting proxy browser usage poses significant challenges due to several factors:
- Traffic Behavior Mimicry: Malicious proxy traffic often resembles legitimate user behavior, making it difficult to distinguish between the two.
- Shared Infrastructure: Attackers often use infrastructure shared with legitimate users, complicating detection efforts.
- Encrypted Traffic: Many proxy browsers use encryption, preventing traditional traffic analysis methods from identifying malicious activities.
- Advanced Evasion Techniques: Attackers employ sophisticated methods, such as rotating IPs and using residential proxies, to evade detection.
3.Defense Measures
To mitigate the risks associated with proxy browser misuse, both enterprises and individuals can implement several strategies:
- Enhanced Traffic Analysis: Utilize advanced analytics to detect unusual traffic patterns indicative of proxy usage.
- Implement CAPTCHA Challenges: Deploy CAPTCHA systems to differentiate between human users and automated scripts.
- Monitor User Behavior: Track user activities to identify anomalies that may suggest proxy usage.
- Adopt Multi-Factor Authentication (MFA): Implement MFA to add an extra layer of security, making it harder for unauthorized users to gain access.
- Educate Users: Conduct training sessions to raise awareness about the risks of proxy browsers and how to recognize potential threats.
- Regular Security Audits: Perform routine security assessments to identify and address vulnerabilities that could be exploited through proxy browsers.
By understanding the types of proxy browsers, recognizing detection challenges, and implementing effective defense measures, individuals and organizations can better protect themselves against the misuse of proxy browsers in cybercrime.
Best Proxy Browsers for Enhanced Privacy and Security in2025
If you're looking to maximize your privacy and enhance your browsing security, a good proxy browser is an invaluable tool. Here are some of the best browsers available today:
1. Recommended Antidetect Browser: DICloak
Key Features and Advantages
DICloak is an advanced antidetect browser designed to manage multiple online accounts securely and anonymously. Compared to typical proxy browsers, it provides additional features like digital fingerprint management and profile isolation, offering a higher level of privacy and security for users who need to manage multiple accounts or bypass detection.
- Profile Isolation: Each browser profile operates independently, ensuring that cookies, cache, and local storage do not overlap between accounts, reducing the risk of cross-contamination and account bans.
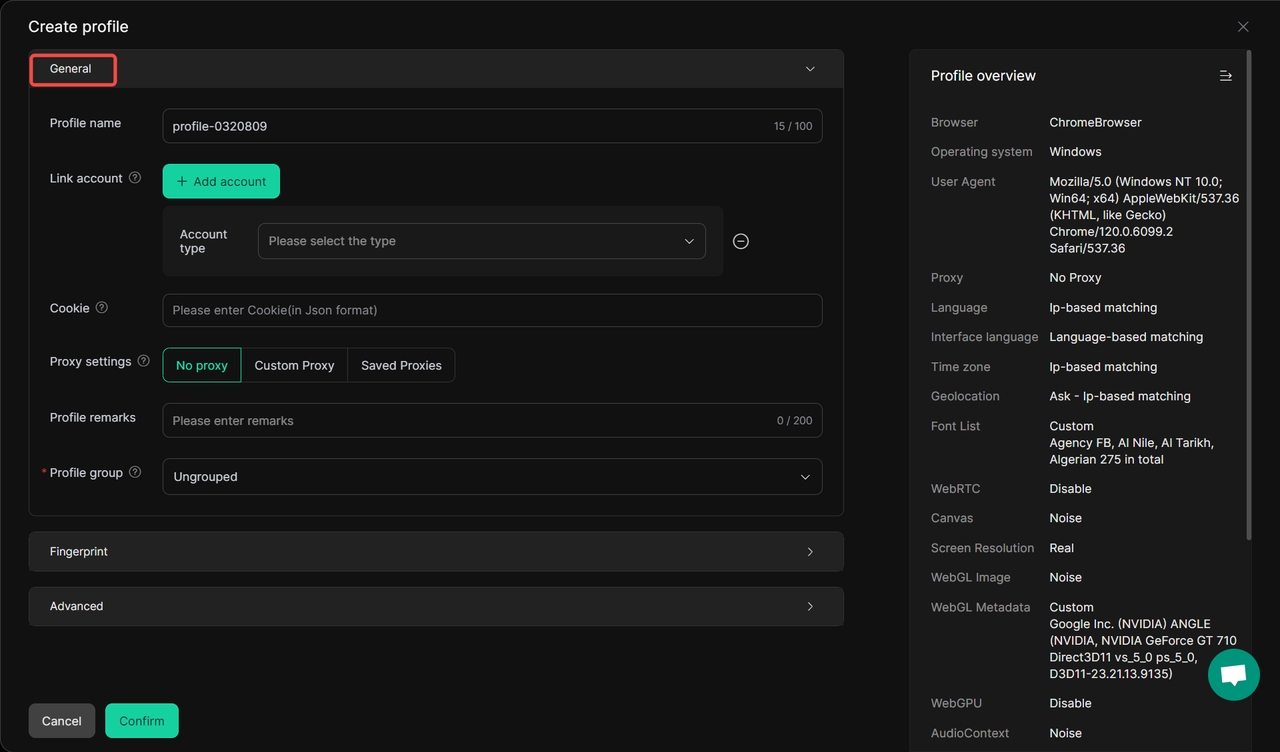
- Proxy Configuration: DICloak supports various proxy protocols, including HTTP, HTTPS, and SOCKS5, enabling users to assign different proxies to each profile for enhanced anonymity.

- Advanced Fingerprint Simulation: DICloak allows users to customize browser fingerprints, including user agents, screen resolutions, time zones, and languages, to create unique digital identities for each account.

- RPA Automation: The built-in Robotic Process Automation (RPA) system allows users to automate repetitive tasks across multiple profiles, saving time and increasing efficiency.
- Team Work Management: DICloak offers features like profile sharing, permission management, and data isolation, facilitating secure teamwork and collaboration.
Common Use Cases
DICloak is utilized across various industries for tasks that require secure and anonymous online activities:
- Social Media Marketing: Manage multiple social media accounts without the risk of bans or detection, ensuring smooth and uninterrupted marketing campaigns.
- E-commerce Operations: Operate multiple online stores or marketplaces simultaneously, maintaining separate identities for each to avoid account suspension.
- Affiliate Marketing: Run numerous affiliate accounts with distinct digital fingerprints, preventing link associations and potential account bans.
- Web Scraping: Collect data from websites without triggering anti-bot measures by rotating profiles and proxies.
Pricing and Plans
DICloak offers a range of pricing plans to accommodate different user needs:
Additionally, you can customize a plan based on your specific needs.
| Plan | Price | Members | Profiles | Daily Open Times | Features |
| Free Plan | $0/month | 1 | 5 | 15 | Customize browser fingerprints, Flexible proxy configuration, Try for Free |
| Share Plan | $8/month | 3 | 50 | 1000 | Includes all Free Plan features, Batch operations, data sync, and more, Team collaboration, ideal for small teams |
| Plus Plan | $28.8/month | 1 | 100 | 50000 | Full feature access, Multi-device login for team members, Supports RPA automation, window synchronization, and more, 1-on-1 account manager support |

2.1Browser
- Features: 1Browser offers complete isolation for each browsing profile, ensuring that your browsing data, cookies, and history remain entirely separate. This makes it perfect for managing multiple accounts across various platforms, such as social media or e-commerce sites, without the risk of cross-leakage.
- Use Cases: Ideal for privacy-conscious users, marketers, and social media managers who need to handle several accounts at once. It also integrates seamlessly with proxies and VPNs to help users bypass geo-restrictions.
- Platform Support: Available on Windows and macOS.

3.Smartproxy X Browser
- Features: With Smartproxy X Browser, you can create unlimited browser profiles, each with a unique digital fingerprint. It also supports traffic encryption and offers one-click mass proxy imports for ease of use.
- Use Cases: Perfect for users needing multiple profiles on the same website or frequently bypassing location-based restrictions, such as those working in e-commerce, social media management, or digital marketing.
- Platform Support: Windows and macOS. Requires a Smartproxy subscription starting at $7.

4.Tor Browser
- Features: Tor offers multi-layered encryption, keeping your browsing activity secure. It automatically clears cookies and browsing history after each session, making it ideal for privacy-focused individuals.
- Use Cases: Best suited for accessing the dark web, bypassing censorship, and keeping browsing activity private in countries where Tor is not banned.
- Platform Support: Windows, Linux, macOS, and Android. Tor is completely free.

5.Hide.me Proxy Browser
- Features: A straightforward and easy-to-use proxy browser from Hide.me, providing 3 free proxies, page encryption, and URL encryption. It’s a simple solution to bypass some geo-restrictions with a moderate level of privacy.
- Use Cases: Great for users who occasionally need to access blocked websites with a decent level of anonymity.
- Platform Support: Web app. Fully free.

6.IPRoyal Proxy Browser Extension
- Features: IPRoyal Proxy Extension turns your browser into a proxy browser, allowing easy switching between multiple proxy profiles. It supports any proxy provider and eliminates the need to adjust system settings.
- Use Cases: Ideal for users who want to switch between various proxies to bypass geo-restrictions, secure browsing on public Wi-Fi, and manage multiple accounts.
- Platform Support: Firefox and Chrome extensions. Free to use with the purchase of proxies.

7.Oxy Proxy Browser Extension
- Features: Oxy Proxy is a browser proxy manager that allows you to switch between multiple proxy profiles easily, with special support for Oxylabs Residential Proxies. It also provides seamless changes to proxy sessions without editing usernames.
- Use Cases: Perfect for users who frequently change proxies or need to manage multiple accounts, especially for avoiding IP bans and blacklisting.
- Platform Support: Android app and Chrome extension. Free to use, with the purchase of proxies.

8.Epic Privacy Browser
- Features: Epic Privacy Browser is a Chromium-based browser that includes an encrypted proxy and anti-tracking features built in. It blocks ads, third-party cookies, and fingerprinting vectors out of the box.
- Use Cases: Ideal for everyday browsing where you want to avoid Google’s tracking and bypass geo-restrictions without using a separate VPN.
- Platform Support: Windows, macOS, Android, iOS/iPadOS. Free.

9.Aloha Browser
- Features: Aloha Browser combines a built-in VPN/proxy, ad-blocker, and file manager with a strong focus on privacy. It also includes an encrypted proxy and supports a zero-log policy.
- Use Cases: Great for secure browsing on public Wi-Fi, streaming, and P2P downloads, especially for mobile users.
- Platform Support: Android, iOS/iPadOS, Windows, and macOS (desktop beta). Free tier with premium options available.

Common Use Cases and Examples
1.Common Use Cases
Privacy Protection
A proxy browser helps protect your online identity by masking your real IP address. This makes it harder for websites, advertisers, and even hackers to track your online activities. For example, using a proxy browser can prevent advertisers from collecting data on your browsing habits, enhancing your privacy.
Bypassing Geo-Restrictions
Many websites and streaming services restrict access based on your geographic location. A proxy browser allows you to access content that may be blocked in your region by routing your internet traffic through a server located in a different country. This makes it appear as though you're accessing the internet from the proxy server's location, enabling you to view region-locked content.
2.Real-World Examples
1.Streaming Services
Streaming platforms like Netflix and BBC iPlayer often have different content libraries for different countries. By using a proxy browser, you can access content available in other regions. For instance, if you're in the U.S. and want to watch a show available only in the UK, a proxy browser can help you access that content.

2.Accessing Restricted Websites
In some countries, access to certain websites is restricted or censored. A proxy browser can help you bypass these restrictions and access the information you need. For example, if you're in a country where social media platforms are blocked, using a proxy browser can allow you to connect to these platforms.

3.Enhanced Security on Public Wi-Fi
Public Wi-Fi networks are often unsecured, making it easier for hackers to intercept your data. Using a proxy browser can add an extra layer of security by routing your internet traffic through a secure server, protecting your personal information from potential threats.

4.Managing Multiple Accounts
If you need to manage multiple accounts on the same website, a proxy browser can help you do so without getting flagged for suspicious activity. By using different proxy servers for each account, you can keep your activities separate and secure.

Choosing the Right Proxy for Your Proxy Browser
Selecting the appropriate proxy is crucial when using a proxy browser to ensure optimal performance, security, and anonymity. Below are the three primary types of proxies commonly used:
1.Residential Proxies
What Are They?Residential proxies use IP addresses provided by Internet Service Providers (ISPs) to homeowners. These proxies appear as regular users to websites, making them ideal for tasks requiring high anonymity.
Best For:
- Web scraping and data collection
- Bypassing geo-restrictions
- Avoiding IP bans and CAPTCHAs
Pros:
- High anonymity and low detection rates
- Access to geo-restricted content
- Reduced risk of IP blacklisting
Cons:
- Higher cost compared to other proxies
- Potentially slower speeds due to shared usage
Example Use Case:
A digital marketer uses residential proxies through a proxy browser to gather competitor pricing data without revealing their identity or triggering anti-bot measures.

2.Data Center Proxies
What Are They?Data center proxies are not affiliated with ISPs and are hosted in data centers. They are faster and more affordable but are easier to detect.
Best For:
- General browsing and accessing public websites
- Automated tasks like SEO monitoring
- Testing website performance from different locations
Pros:
- Cost-effective and high-speed connections
- Suitable for bulk tasks and automation
Cons:
- Higher risk of detection and blocking
- Limited access to geo-restricted content
Example Use Case:
A developer utilizes data center proxies with a proxy browser to test a website's load times from various regions without revealing their actual location.

3.Mobile proxies
What Are They?Mobile proxies route traffic through mobile carriers, making them appear as if accessed from a mobile device. They are less likely to be detected due to their legitimate nature.
Best For:
- Managing multiple social media accounts
- Accessing mobile-specific content
- Bypassing mobile-specific geo-restrictions
Pros:
- High legitimacy and low detection rates
- Access to mobile-specific content and services
Cons:
- Higher cost and potentially slower speeds
- Limited availability compared to other proxy types
Example Use Case:
A social media manager employs mobile proxies with a proxy browser to operate multiple Instagram accounts without risking bans or CAPTCHAs.

FAQs
1.What Is a Proxy Browser?
A proxy browser is a specialized web browser that routes your internet traffic through an intermediary server, known as a proxy. This setup masks your real IP address, enhancing privacy and allowing you to access content as if you're browsing from a different location. It's particularly useful for managing multiple online accounts, bypassing geo-restrictions, and protecting personal information.
2.Can I Use a Proxy Browser for Free?
Yes, DICloak offers a 7-day free trial. You can add the official customer service and completing a survey to gain trial access.
In summary, a proxy browser is a valuable tool for enhancing privacy, managing multiple accounts, and bypassing geo-restrictions. DICloak stands out with its unique features like profile isolation and proxy integration, making it an excellent choice for secure online activities. However, as with any proxy service, it's crucial to choose a trusted provider. DICloak offers a balance of privacy, usability, and cost-effectiveness, ensuring that your online activities remain safe and anonymous.