What is a proxy?
A proxy is a technical means of forwarding network requests through an intermediary server, which can act as a "bridge" between the user and the target website or server. When you visit a website, your device is usually connected directly to the destination server, but with a proxy, all network requests are processed through the proxy server, which then forwards the request to the target website. The destination server will only see the IP address of the proxy server and will not be able to identify the user's real IP.

The role of proxies is not limited to simple "alternative" requests, it plays an important role in modern Internet applications, and is widely used to improve anonymity, bypass geo-restrictions, improve security, and many other aspects.
Core functions and purpose of use of the agent:
- Hide your real identity and improve anonymity: When using a proxy, the user's real IP address is hidden, and the target website can only see the IP of the proxy server. This will prevent tracking and protect your privacy, especially if you're dealing with sensitive data or if you need to browse anonymously.
- For example, when you're using public Wi-Fi, proxies can provide a stealthy access path for your devices, reducing security risks from exposure to open networks.
- Bypass geo-restrictions and access restricted content: Some websites or streaming services (such as Netflix, Hulu, BBC iPlayer, etc.) restrict access based on a user's geographic location. Through proxies, users can bypass these restrictions by pretending to be visitors from other regions. For example, a user located in China accesses Netflix content in the United States through a US proxy server.
- This technology makes it easier to access data across borders, especially on some streaming media, news sites, or social platforms, where users often use proxies to break through these content blockades.
- Improve Internet speed and stability: Some types of proxies, such as caching proxies, can cache frequently visited website content, reducing load times and improving access speed. If you visit the same website frequently, the proxy server may cache some of the content of this website, and the next time you visit, the proxy server can directly serve the cached content to avoid downloading it again, which greatly improves the loading speed of the web page.
- Multi-account management to prevent account bans: Many platforms, especially social media and e-commerce platforms, often restrict the creation of multiple accounts from a single IP address, deeming it abusive or fraudulent. Through proxies, users can obtain different IP addresses, so as to avoid the risk of account banning caused by the frequent creation of multiple accounts with the same IP.
- For example, if multiple merchants on an e-commerce platform use the same IP to operate, the platform may be regarded as abnormal behavior, and the account may be restricted. If you use a proxy, you can use a different IP address for each account, reducing the risk of being banned.
Specific types of agents:
- HTTP proxy: Mainly used for web browsing, processing requests through the HTTP protocol, suitable for web access and other application scenarios.
- SOCKS proxy: Supports more protocols, not just limited to HTTP. It is suitable for scenarios that require more flexibility and can handle multiple network requests (such as FTP, P2P, SMTP, etc.).
- Transparent proxies: Typically used for caching content or access control, users may not be aware they are using a proxy.
- Anonymous proxy: The real IP of the user is hidden through the proxy, but the server will still know that you are using a proxy to access.
- High anonymity proxy: In addition to hiding your real IP, the server has no way of knowing whether you are using a proxy or not, so it is completely anonymous.
- The specific choice of agent will vary depending on the purpose and needs of the agent. For example, if you need to hide your identity and avoid being detected by the platform using a proxy, a highly anonymous proxy is a better option. If you're just looking for faster web page loading, an HTTP proxy will do the trick.
What are static IPs and dynamic IPs?
IP address(Internet Protocol address) is a unique identifier for each networked device on the network, like a mailing address for a house, used to indicate the device's network location. An IP address allows a device to communicate with other devices, servers, or internet services. In day-to-day use, there are two main ways to assign IP addresses:Static IPandDynamic IP, which differ significantly in terms of stability, cost, security, and use cases.
Static IP
Static IPA fixed IP address is a fixed IP address that is manually assigned by an Internet Service Provider (ISP) that, once assigned to a device, remains the same whenever and wherever the device reconnects to the network. As a result, static IPs are ideal for devices and services that require long-term, stable connectivity, such as corporate servers, remote monitoring systems, virtual private networks (VPNs), or network devices that require external access.
Dynamic IP
Dynamic IPA temporary IP address is assigned through the Dynamic Host Configuration Protocol (DHCP). Whenever a device connects to a network, the ISP or router randomly assigns a usable IP address, which may be reassigned to another device after the device is disconnected from the network. This flexible allocation makes dynamic IP a mainstream choice for home networks and small businesses.
The difference between a dynamic IP and a static IP
Dynamic IPandStatic IPThere are two different IP address assignment methods, each with different characteristics and application scenarios. Below we will compare their differences in detail from multiple perspectives.
1.Distribution
- Dynamic IP: Dynamic IP addresses are dynamically assigned through the Dynamic Host Configuration Protocol (DHCP). Each time a device connects to the network, the Internet Service Provider (ISP) or local router assigns a temporary IP address to the device as needed. The IP address of the device may change each time you disconnect from the network and reconnect.
- Static IP: A static IP address is manually assigned to a device by an ISP or network administrator and remains the same for a long period of time. Regardless of how the device is connected to the network, the static IP remains fixed at all times.
2.stability
- Dynamic IP: Since IP addresses are dynamically assigned, you may get a new IP address every time you reconnect. This means that dynamic IPs are less stable, especially in scenarios where a fixed connection is not required.
- Static IP: The static IP address does not change, providing a high degree of stability. It is suitable for applications that need to be online for a long time and do not want to change the IP address, such as servers, remote access, monitoring devices, etc.
3.security
- Dynamic IP: Since dynamic IP changes with each connection, it increases the privacy and security of surfing the web. It is difficult for hackers to trace the real identity of a user because the IP address changes frequently. This makes dynamic IPs more secure for the average home user and individual in terms of attack prevention and privacy protection.
- Static IP: Since the static IP address is fixed, if the attacker knows the IP address, he can track and attack the target device for a long time. While a static IP can be useful in providing a stable service, it can also increase the risk of exposure, especially in the absence of other security safeguards.
4.cost
- Dynamic IP: Usually provided for free by ISPs. Dynamic IPs come at no additional cost and are assigned by default to most home and small business users. Most home broadband services use dynamic IP.
- Static IPs: Static IPs usually come at an additional cost. ISPs often charge additional fees for static IPs because they require more resources to provision, maintain, and manage, and because they provide continuous, long-term network connectivity.
5.Applicable scenarios
- Dynamic IP: suitable for home users and general Internet needs. Dynamic IPs are sufficient for most situations, especially for short-term connections such as daily surfing, web browsing, and video watching.
- Static IP: suitable for application scenarios that require long-term stable connections, such as servers, website hosting, remote desktops, VPN connections, and video surveillance systems. If you need to let other devices or users access your device or service through a fixed address, a static IP is the best option.
6.Network management
- Dynamic IP: Because the IP address changes dynamically, the user cannot accurately predict the IP address that the device will get each time you connect. This won't be too much of a problem for home users, but it can add complexity to management for applications that require a fixed IP, such as VPNs, remote desktops, etc.
- Static IP: Static IP addresses are easy to manage, especially for businesses or users who need to manage devices remotely. Static IPs allow network administrators to more clearly arrange and manage device access and network configurations.
7.Configuration and maintenance
- Dynamic IP: For most users, the configuration of dynamic IP is done automatically without user intervention. Users only need to connect to the network and an IP address will be automatically assigned.
- Static IP: Configuring a static IP usually requires manual address entry and may involve modifying the network settings of the router or device. If you need more than one static IP address, you may also need to request from your ISP and configure the appropriate settings.
| peculiarity | Dynamic IP | Static IP |
| Distribution | Dynamic allocation, automatic allocation through the DHCP protocol | Manual dispensing, which remains unchanged for a long time |
| stability | IP addresses can change and become unstable | The IP address is fixed and provides a stable connection |
| security | IP addresses change frequently, and security is high | The IP address is fixed, making it easy for attackers to track and lock down |
| cost | Usually free of charge with no additional costs | Additional fees apply |
| Applicable scenarios | Daily Internet access, home users, small businesses | Devices that require a stable connection, such as servers, remote access, monitoring devices, etc |
| Network management | It is not suitable for fixed management, and the IP address changes frequently | It is easy to manage and suitable for scenarios that require a fixed IP address |
What is Shared Proxy SOCKS?
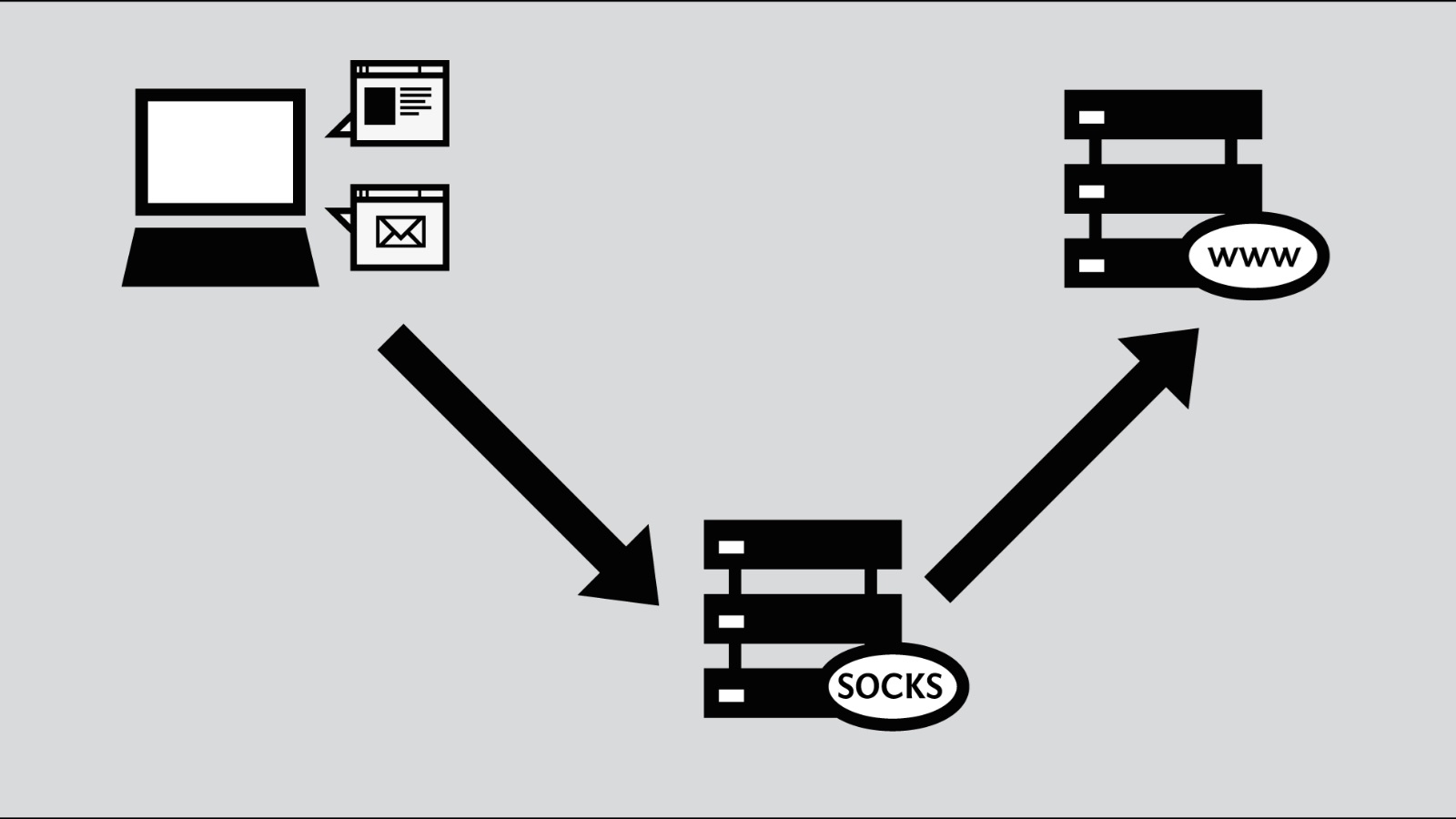
Shared Proxy SOCKS(Shared Proxy SOCKS) is a proxy server that passes throughSOCKS protocolForward the user's traffic to the target website or service. SOCKS (Socket Secure) is an underlying network protocol that can deliver network traffic through proxy servers and support a variety of applications, such as browsers, email clients, FTP clients, etc.Shared proxiesThis means that multiple users share the same IP address.
1.Overview of the SOCKS protocol
SOCKS is a different protocol from traditional HTTP proxies that offers greater flexibility and compatibility. SOCKS proxies can handle any type of network traffic and support multiple protocols (e.g., TCP, UDP), making them more versatile than HTTP proxies. The main versions of the SOCKS protocol are SOCKS4 and SOCKS5, where:
- SOCKS4: The initial version, which supports the TCP protocol, has relatively simple functions and cannot be authenticated.
- SOCKS5: Improves on SOCKS4 and supports more features, including authentication, stronger security, UDP protocol support, and more.
- Shared proxiesThis means that multiple users will share a single IP address through the same proxy server. In other words, the traffic of multiple users will be forwarded through the same proxy, and the target website or service can only see the IP address of the proxy, but cannot know the real source of the traffic.
2.Shared Proxies Features of SOCKS
- Shared IP addresses by multiple users: Unlike Private Proxies, shared proxies share IP addresses by multiple users. Each user accesses network resources through the same proxy server, which can save the cost of proxy services, but may affect the stability and speed of use.
- Support for a wide range of applications: SOCKS proxies can handle a variety of protocols, and in addition to web browsing, they can also be used for FTP, mail transfer, video streaming, and more. As a result, SOCKS proxies are more applicable than HTTP proxies in general.
- Lower cost: The cost of a shared proxy is usually lower because multiple users share the same proxy IP address. This method is suitable for users who do not need frequent access and do not require high anonymity.
3.Shared Proxies pros and cons of SOCKS
Merit:
- Low cost: The biggest advantage of shared proxies is that they are less expensive. Because multiple users share the same IP address, operators can spread this part of the cost to multiple users, making the cost per user low.
- Wide range of applications: SOCKS proxy supports a variety of protocols and applications, and is suitable for a variety of network operations, such as browsing the web, downloading files, using P2P, etc.
- Provides some anonymity: When using a shared proxy, the target website can only see the IP address of the proxy server, and cannot directly trace the user's real IP address, which adds a certain amount of privacy protection.
- Shortcoming:
- Shared IPs can lead to blocking: Since multiple users share the same IP address, the entire IP address may be blocked by a website if the behavior of one of the users is considered unusual or malicious. In this case, all users using the IP address will be affected.
- Slow speeds: With multiple users sharing the same proxy IP address, traffic can be overloaded, resulting in slower access, especially during peak hours or high loads.
- Not suitable for tasks that require high anonymity: The IP address of a shared proxy is already used by multiple users, so it is less anonymous and a website may recognize it as a proxy IP. For some scenarios that require high anonymity, such as circumventing strict anti-fraud mechanisms, shared proxies may not be the best choice.
4.How to choose a shared proxy SOCKS
When choosing a shared proxy SOCKS, users need to pay attention to the following:
- Credibility of proxy providers: Choosing a reputable proxy service provider can reduce blocking and provide more stable proxy services.
- Proxy speed and stability: Since multiple users share the same IP address, the speed and stability of a shared proxy can be affected by the load. When choosing, one should evaluate the quality of the network provided by the proxy service provider, the geographical location of the server, etc.
- Usage limits: Find out if the service provider has limits on traffic or the number of connections, and how long the proxy will be available.
- IP Blocking Risk: If multiple users share the same IP address, the IP address may be blocked due to the abnormal behavior of a user, affecting the user experience of other users. Choosing a reputable provider can effectively reduce this risk.
What is a residential address IP?
**Residential IPrefers to:Internet Service Providers (ISPs)** provide IP addresses to the average household user, which are tied to a home address and are typically used to surf the Internet at home. This type of IP address has higher reliability and legitimacy and is usually obtained through a home broadband connection.
Residential address IP withData center IP address(Also known as.)Commercial IPThe biggest feature is its origin and use. A residential address IP is an IP that comes from a home user in the true sense of the word, and it represents a physical address that is usually used for personal or household Internet use. The allocation of such IPs is provided to ordinary households or individuals through ISPs.
1.Characteristics of residential address IPs
- Ordinary home broadband connection from an ISP: A residential IP is a common IP address provided by an ISP to home users, usually obtained through a broadband connection. These IP addresses are directly related to the residential address of the average home user.
- Higher reliability: Because these IP addresses are assigned from the ISP to home users, they are usually not easily blocked or blocked, and are often more "trusted" than commercial or data center IPs.
- Not easily recognizable as a proxy: Residential IPs are often not recognized as proxy servers or VPNs by websites or services. This is because they are obtained from a home network and not delivered through a virtual network service or data center server. As a result, residential IPs tend to be more effective than other types of IPs when it comes to bypassing geo-restrictions or browsing anonymously.
2.Advantages and disadvantages of residential address IPs
Merit:
- Harder to block: Because residential IPs are associated with the home address of the average home user, websites usually don't restrict access to those IPs, so residential IPs are more reliable when bypassing geo-restrictions.
- Less recognizable as a proxy: Residential IPs are not as easily identified as data center IPs or VPN addresses, so they are suitable for scenarios that require a high degree of concealment, such as bypassing content filtering and improving anonymity.
- Higher levels of trust: Some websites and online services may place more trust in residential IPs because they believe that they represent real user behavior rather than traffic going through virtual servers or proxies.
- Shortcoming:
- Higher price: Residential IPs are generally more expensive than other types of IPs, such as data center IPs or shared proxies, because they need to be rented or purchased from an internet service provider and are usually charged by traffic or duration.
- Limited quantity: The supply of residential IPs is limited, especially for scenarios with a large number of IP demand, and it may become difficult to obtain enough residential IP addresses.
3.How to get a residential address IP
There are usually two ways to get a residential address IP:
- Direct purchases: Some service providers allow users to purchase residential address IPs, which are usually obtained from home broadband networks and are more expensive, but are suitable for scenarios that require a high degree of stealth and anonymity.
- Proxy services: Some proxy providers specialize in providing residential proxy IPs, which are obtained from real home addresses rather than through virtual servers. Users can rent these residential IPs to bypass blocks, increase anonymity, and more.
Residential address IP relationship with shared proxy
In the use of web proxies,Residential address IPandShared proxiesThere are significant differences, and these differences are mainly reflected in the source of the IP address, anonymity, usage scenarios, etc. Understanding their relationship can help users choose the right proxy service for their needs.
1.The basic difference between a shared proxy and a residential address IP
- A shared proxy is a service where multiple users share the same proxy IP address. All users who use the proxy will be connected to the network through the same IP, and the target website can only see the proxy IP address, and the user's real IP cannot be traced.
- A residential IP is an IP that is bound to the physical address of an ordinary household user. These IPs are usually assigned to home users by Internet Service Providers (ISPs) for daily online activities. Since they are often considered "real" IPs and are not as easily identified as proxy services like data center IPs or proxy IPs, residential address IPs are often considered more legitimate and stable.
2.Application scenarios for residential IP addresses and shared proxies
- Bypass IP Blocking and Regional Restrictions: The IP address of a shared proxy is easily recognized as a proxy IP by the target website due to the shared use by multiple users, making it more susceptible to blocking. On the other hand, residential IP addresses are usually bound to the addresses of home users, and it is difficult for the target website to distinguish whether it is a proxy or not. As a result, residential IPs are more reliable than shared proxies when it comes to bypassing regional restrictions and IP blocking.
- For example, when you use a shared proxy to access certain websites, the website may detect high usage of the IP and consider it a proxy service to restrict access. Conversely, when using a residential address IP, the website will see the IP of an average home user and will not usually block it.
- Social media management and automation: For some tasks that require multiple accounts, such as social media management or bulk operations on e-commerce platforms, when using a shared proxy, multiple users sharing one IP may result in frequent IP monitoring and banning. Residential IP addresses, on the other hand, can provide higher stability due to their "real" attributes and reduce the risk of being banned. As a result, residential address IPs behave more naturally in these scenarios.
- Crawling and data scraping: For large-scale data scraping, using shared proxies can run the risk of blocked IPs, especially if the scraping target website has strict detection of proxy IPs. Residential address IPs are able to reduce these risks because they are not usually considered proxy servers. Residential IP provides higher reliability and longer lifespan when scraping data at scale.
3.Shared proxies with residential address IP security and privacy
- Security: The IP address of a shared proxy is usually public, and multiple users share the same IP, resulting in frequent use and easy identification and blocking by the target website. On the other hand, the users of residential address IPs are ordinary home users and are usually not exposed to public networks, so they are generally better than shared proxies in terms of security.
- Privacy: Residential address IPs are often considered "real" IP addresses due to their binding to the actual address of home users, which makes it more natural and less easily traceable when accessing certain services that require high anonymity. However, because the IP address of a shared proxy is shared by multiple users, it may be identified as a proxy server by the website, which will affect the privacy of the user.
4.Cost comparison
- The cost of shared proxies is relatively low, making them suitable for users who don't have high requirements for IP stability and anonymity. Since multiple users share the same IP, proxy service providers are able to spread the cost and offer a lower price.
- The price of residential address IPs is relatively high because these IPs are usually provided by ISPs and are assigned to specific home users. Due to their high anonymity and low risk of blocking, residential address IPs are often more expensive than shared proxies.
How to add a proxy
Setting up a proxy for your browser is an important way to protect your privacy, bypass regional restrictions, or optimize your web access. Here are the detailed steps, using Google Chrome and Microsoft Edge as examples to help you successfully complete the proxy configuration.
Step 1: Open your browser's settings page
- Google Chrome: Open the Chrome browser and click on the "three-dot menu" in the top right corner (usually located to the right of the address bar). In the drop-down menu, select Settings.
- Microsoft Edge: Open the Edge browser and click the "three-dot menu" in the upper right corner. Select Settings in the menu.
Step 2: Find the proxy setup portal
In your browser's settings page, search for proxie-related options:
- Use the Search Bar: Enter Proxy Settings in the search box at the top of the settings page. Click the "Open Agent Settings for Computer" link displayed in the results to jump to the system proxy settings.
- Direct navigation: On the settings page, click "System & Performance" > "Open Agent Settings for Computer" (it may appear as "Network Settings" in Edge).
Step 3: Go to System Proxy Settings
The browser's "Proxy Settings" will actually jump to the operating system's proxy configuration interface, as follows:
- Windows: In the pop-up "Network & Internet Settings" window, click "Proxy" in the left menu. You'll see a page with "Automatic Proxy Setup" and "Manual Proxy Setup".
- Mac: Jump to System Settings > Network. Select the network you are currently connected to and click on the "Advanced" > "Agent" tabs.
Step 4: Configure manual agents
- Windows: Scroll down to the "Manual Proxy Settings" section. Find the "Use Proxy Server" option and toggle it to "Enabled". In the appropriate text box, enter the following information: Proxy address: e.g. 192.168.1.1 Port number: e.g. 8080 Once you have confirmed that everything is correct, click the "Save" button.
- Mac: Select the proxy type (e.g., HTTP, HTTPS, SOCKS) that needs to be enabled. In the text box on the right, enter the proxy server address and port number. Click "Apply" to save the changes.
Step 5: Test the proxy connection
- Open a web page, for examplehttps://whatismyipaddress.com/。
- Check if your IP address has changed. If the displayed IP is the same as the proxy server address, the proxy has been successfully enabled.
Frequently Asked Questions About Proxies
1. What is a proxy?
A proxy is an intermediary server that sends web requests on behalf of the user and forwards them to the target website, hides the user's real IP address, provides anonymity, bypasses geo-restrictions, and more.
2. What are the types of proxies?
The main types of proxies include HTTP proxy, SOCKS proxy, transparent proxy, anonymous proxy, and high anonymity proxy, etc., which are suitable for different usage needs.
3. What is the difference between a static IP and a dynamic IP?
The static IP address is fixed and suitable for scenarios that require a stable connection. The dynamic IP address changes with each connection, making it suitable for the average home user.
4. What are the pros and cons of shared proxy SOCKS?
Shared proxy SOCKS supports multiple protocols and is less expensive, but it can lead to slowdowns and the risk of being blocked because multiple users share the same IP address.
5. How do I choose the right proxy?
When choosing a proxy, you should choose the right type according to your needs, pay attention to the stability, speed and anonymity of the proxy, and make sure to choose a reputable proxy service provider.