With the popularization of the Internet and the increasingly serious problem of network security, how to protect personal privacy and anonymity has become the focus of attention of many netizens. Traditional proxy services, such as HTTP proxies, can help users hide their IP addresses to a certain extent, but their functions and application scenarios are relatively limited. As an advanced proxy protocol, SOCKS5 proxy has gradually become an ideal choice for users to protect network privacy and overcome geographical restrictions due to its strong anonymity, ability to support multiple protocols, and efficient data transmission characteristics.
This article will answer your questions about proxies, introduce the basic principles, benefits, and common application scenarios of SOCKS5 proxies, and help you fully understand the potential and real economic value of this technology.
What is a SOCKS5 proxy?
SOCKS5 (Socket Secure Version 5) is an advanced proxy protocol that is commonly used to hide users' real IP addresses and protect their online privacy. When you make a request through a SOCKS5 proxy, the proxy replaces your real address with its own IP address, masking the user's online identity and keeping personal information safe. Unlike traditional HTTP proxies, SOCKS5 proxies don't just handle HTTP requests, they also support a variety of protocols and applications, such as FTP, SMTP, P2P, streaming, and more, so it's more widely used in a wide range of scenarios. Due to the anonymity and efficiency of SOCKS5 proxies, it is seen as an effective solution for cybersecurity, especially if it does not involve sensitive data, providing better speed and stability.

How SOCKS5 works
The SOCKS5 proxy works in the following steps:
- Client-initiated requests: You use a SOCKS5 client (e.g., browser plug-in, torrent client, etc.) in a browser, game client, or other application to initiate a connection to a SOCKS5 proxy server.
- Proxy connection: The SOCKS5 proxy receives the request and verifies the client's identity (if required), then establishes a TCP or UDP connection to the destination server.
- Traffic forwarding and processing: When a traffic is sent from a client, the SOCKS5 proxy processes the data (e.g., hiding the real IP) and forwards the traffic to the destination server. During this process, the agent does not decrypt or modify the transmitted content, keeping the data in its original state.
- Response Return: The destination server processes the request and returns the response information to the client via the SOCKS5 proxy. At this point, the destination server has no way of knowing which user the request is coming from, because the request has been forwarded and disguised by the proxy server.
Features of SOCKS5 Proxies:
- Supports multiple protocols: The SOCKS5 proxy not only supports HTTP requests, but also handles multiple protocols such as FTP, SMTP, POP3, DNS queries, and is suitable for a wider range of application scenarios.
- High anonymity: It hides the user's real IP address and doesn't modify the content while forwarding the data, which makes it a relatively safe choice, especially for users who want a high level of anonymity.
- No data modification: Unlike HTTP proxies, SOCKS5 proxies do not need to view or modify transmitted packets, so it does not leak information or alter the content of data, providing greater privacy.
- Compatibility: SOCKS5 is compatible with a wide range of applications, including browsers, instant messaging software, FTP clients, video streaming, and P2P downloading tools, making it suitable for a wide range of scenarios.
Application scenarios for SOCKS5
SOCKS5 proxies are widely used for both individual and business users, and the following are some common use cases:
- Improve online anonymity: If you're looking for privacy, SOCKS5 is ideal. It effectively hides the user's IP address and is suitable for scenarios that require anonymity, such as accessing restricted websites and bypassing geoblocks.
- Bypass geo-restrictions: With SOCKS5 proxies, users can easily bypass all kinds of geo-restrictions and access blocked or restricted content. This is great for websites that want to watch videos on a global scale or visit a specific area.
- Support for P2P and streaming apps: SOCKS5 proxies are great for P2P file sharing (like torrent downloads) and streaming apps. Due to its fast processing speed and lack of interference with data transfer, this makes it ideal for these activities.
- Enterprise remote access: Enterprises can leverage SOCKS5 proxies to provide secure access to remote users. With SOCKS5 proxies, employees can connect to the company's intranet without having to modify the company's firewall rules, ensuring data security.
- Data Mining & Social Media Marketing: Some businesses use SOCKS5 proxies for data mining, search engine optimization (SEO), social media marketing, and more, with the help of multiple proxies for crawling, analysis, and content publishing at scale.
- Improved gaming experience: For online gamers, SOCKS5 proxies can help improve the gaming experience, reduce lag, and hide real IPs from being banned from gaming platforms.
SOCK5 link format
The SOCK5 link format typically follows the following structure and is specifically dependent on the support of the application or tool:
Basic format
socks5://:@:
Parameter description
- socks5://: The name of the protocol, which indicates the use of SOCKS5 proxy.
- : The username of the agent, if authentication is required.
- : The agent's password, if authentication is required.
- : The hostname or IP address of the proxy server.
- :代理服务器的端口号(通常是 1080)。
example
1. If an authentication SOCKS5 proxy is required:
socks5://user123:pass456@192.168.1.100:1080
2. If you don't need a SOCKS5 proxy for authentication:
socks5://192.168.1.100:1080
SOCKS5 with encryption (combined with HTTPS)
Some tools support the use of SOCKS5 with HTTPS, and you can specify the following forms of links in your browser, SSH tunnel, or other supported apps:
socks5h://:@:
- socks5h://: This format is used to resolve DNS queries through the SOCKS5 proxy, ensuring that the proxy handles DNS requests.
Application scenarios
- You can enter when you manually configure the proxy in your browser
- Use the full URL format directly in tools that support SOCKS5 links, such as cURL or wget.
- Please make sure to fill in the correct username, password, IP address, and port number according to the requirements provided by the proxy service provider to ensure a successful connection.
Advantages of using SOCKS5 proxies
As a flexible, efficient, and multi-application proxy protocol, SOCKS5 proxy has many unique advantages over other types of proxy servers (such as HTTP proxy, etc.). Here are the main advantages of SOCKS5 proxies:
1.Efficient data transfer
SOCKS5 proxies do not have an encryption layer at the time of data transfer and forward packets directly, so there is no additional resource consumption due to encryption and decryption operations. This means that when using SOCKS5 proxies, the transfer speed will be relatively fast and the latency will be low, especially for applications that require high-speed transfers, such as streaming, large file downloads, or online gaming.
- No encryption overhead: Because SOCKS5 does not encrypt, there is no additional computational burden on packets as they travel between the proxy server and the destination server. As a result, it offers faster speeds than other crypto proxies, especially in bandwidth-limited network environments.
- Ideal for real-time applications: For applications that require real-time reactions, such as video calls, online gaming, etc., the speed advantage of SOCKS5 makes it an ideal choice.
2.Cost-effective
SOCKS5 proxies are generally more affordable. SOCKS5 proxies do not require additional encryption and complex security processing, which makes it less expensive to operate.
- Lower subscription fees: SOCKS5 proxies are usually less expensive to serve, making them suitable for users with a more limited budget.
- Low resource requirements: Because SOCKS5 does not involve complex cryptographic algorithms, it requires fewer computing resources, which allows it to keep costs low when handling large numbers of concurrent connections.
3.Application-level agents
One of the biggest advantages of SOCKS5 proxies is its flexibility. You can configure different applications to use the SOCKS5 proxy as needed. Whether it's a browser, a P2P client, a video streaming platform, an instant messaging software, or a gaming client, SOCKS5 proxies can be set up separately to communicate. This means you can tailor your proxy settings to different applications and network environments to ensure efficiency and security.
- Flexible configuration for different applications: For example, you can configure SOCKS5 proxies only for applications that require anonymity (e.g., torrent clients), and not for other applications that don't involve sensitive information, such as browsers.
- Support for multi-protocol applications: SOCKS5 proxy supports multiple protocols such as HTTP, FTP, SMTP, POP3, etc., which is suitable for a wider range of application scenarios, so it is more versatile and flexible than other traditional proxies.
4.Bypass geo-restrictions
With SOCKS5 proxies, you can easily bypass geo-restrictions and access blocked or restricted content. Many streaming platforms (e.g., Netflix, Hulu, YouTube) impose geo-region restrictions based on the user's IP address, and SOCKS5 proxies can bypass these restrictions by replacing your IP address.
- Bypass web blocks: By using SOCKS5 proxies, users can access websites or services that are blocked by their country or region, bypassing internet censorship and firewalls.
- Access to global content: For example, you can use a SOCKS5 proxy to access a country-specific Netflix library, or a streaming service that is exclusive to other regions.
5.Built-in security and authentication features
While the SOCKS5 proxy itself is not encrypted, it offers built-in authentication to ensure that only authorized users can connect to the proxy server. This enhances its security, especially in applications that require high privacy protection.
- Authentication mechanism: SOCKS5 proxies support username and password authentication, ensuring that only the right users can send traffic through the proxy server. This effectively prevents unauthorized users from abusing the proxy service and increases security.
- Protected anonymity: With SOCKS5 proxies, the user's real IP address is hidden behind the proxy server, providing an extra layer of privacy.
Common applications of SOCKS5 proxies
As an efficient and flexible proxy tool, SOCKS5 proxies have a wide range of applications in multiple fields. Here are some common SOCKS5 proxy use cases that demonstrate the important role SOCKS5 proxies play in everyday network activities:
1.Anonymous web browsing
SOCKS5 proxies are effective in hiding the user's real IP address, making them ideal for anonymous browsing for many people. Unlike traditional HTTPS proxies, SOCKS5 proxies don't involve encrypted traffic and are suitable for users who want to remain anonymous, but don't need additional encryption.
- Concealing real identity: Users can use SOCKS5 proxies to prevent websites from tracking their real location or identity, which is great for privacy.
- No Encryption Burden: Despite not providing encryption, SOCKS5 still protects the user's anonymity by changing the IP address and is more efficient.
2.Bypass network restrictions
SOCKS5 proxies help users bypass access restrictions set by local or network service providers. This feature is very helpful for accessing internet content in highly censored environments, such as web blocking by companies, schools, or governments.
- Break Firewalls and Censorship: With SOCKS5 proxies, users can bypass geo-blocking, web censorship, and regional restrictions to easily access restricted websites and content.
- Freedom to browse: For example, in China or other countries with strict internet restrictions, SOCKS5 proxies help users access censored content and maintain a free flow of information.
3.Remotely connect to your local network
SOCKS5 proxies have important applications in remote work scenarios. Remote workers can use SOCKS5 proxies to connect to the company's internal network and securely access corporate resources without directly exposing internal IP addresses or modifying corporate firewall settings.
- Secure remote access: Employees can connect to the company's internal network through the SOCKS5 proxy to access data, transfer files, and more, ensuring the security of remote work.
- Avoid complex configurations: Compared to other remote access methods, SOCKS5 proxies are relatively easy to configure and do not have complex encryption layers, reducing resource consumption.
4.Web scraping
SOCKS5 proxies play an important role in large-scale data scraping tasks, especially when large amounts of web page data need to be accessed through a large number of different IP addresses. By using SOCKS5 proxies, bots are able to scrape data more efficiently and avoid being blocked by targeted websites.
- Prevent blocking: Using a SOCKS5 proxy ensures that each request comes from a different IP address, which helps avoid IP bans due to frequent requests.
- Improve scraping efficiency: SOCKS5 proxy can provide fast and stable connections, reduce the delay of crawler data scraping, and optimize data collection efficiency.
5.Search engine optimization and market research
Marketers, SEO experts, and market researchers often use SOCKS5 proxies to analyze search engine results, user behavior, and market trends in different regions. By switching proxies to a different country or region, users can simulate local access and thus obtain accurate geo-targeted data.
- View regional search results: With SOCKS5 proxies, users can simulate IP addresses in different regions and view local search engine results to see changes in search rankings.
- Accurate market research: Use SOCKS5 agents to conduct market analysis to understand the needs of users in different regions for products or services, so as to provide data support for marketing activities.
6.Online games
SOCKS5 proxies are widely used in online games, especially for those looking to improve their gaming experience and reduce lag. By connecting to a SOCKS5 proxy that is closer to the game server, players can significantly reduce latency and improve the smoothness of the game.
- Optimize game latency: For online gamers, connecting to a SOCKS5 proxy closer to the game server can reduce the latency of packet transmission and improve the responsiveness of the game.
- Break through regional restrictions: Some online games will set server restrictions on players in different regions, and players can use SOCKS5 proxies to connect to servers in other regions and participate in international battles.
Difference Between SOCKS5 Proxies and Other Proxies
SOCKS5 proxy is a widely used proxy protocol that has some distinct differences compared to other common proxies such as HTTP proxies and HTTPS proxies. Here are the main differences between SOCKS5 proxies and other types of proxies:
1. Supported Protocols
SOCKS5 proxy: Supports multiple protocols such as TCP and UDP. It is capable of handling any type of traffic, whether it's web browsing, file transfers, or real-time messaging or online gaming. HTTP proxy: Only HTTP and HTTPS traffic are supported, and typically only HTTP protocol-based activities such as web browsing can be handled. HTTPS proxy: HTTPS traffic that is specifically used to encrypt and is usually limited to encrypted connections and cannot handle other protocols such as FTP or UDP.
2. Encryption and Privacy Protection
SOCKS5 proxy: Does not encrypt traffic, but is only responsible for forwarding traffic to the destination server. It's more focused on obscuring identities and increasing speed than providing encryption or extra security. HTTP/HTTPS proxies: While HTTP proxies don't encrypt traffic, HTTPS proxies encrypt the data transfer process. HTTPS proxies provide some security when browsing the web, especially against man-in-the-middle attacks (MITM).
3. Performance
SOCKS5 Proxies: With no encryption or additional processing, SOCKS5 proxies typically offer higher speeds and are suitable for activities that require high bandwidth and low latency, such as online gaming, P2P downloads, and more. HTTP/HTTPS proxy: The process of encrypting or processing HTTP requests adds some latency, especially for HTTPS proxies, which are typically less performant because they need to handle SSL/TLS encryption.
4. Applicable Scenarios
SOCKS5 Proxies: Ideal for applications that require high-speed and multi-protocol support, such as P2P downloading, streaming, online gaming, and more. With UDP support, SOCKS5 is especially suitable for real-time applications such as VoIP or online gaming. HTTP proxy: Better suited for web browsing and handling HTTP-based tasks. It's effective for caching optimization and content filtering while browsing the web, but it's not suitable for other types of traffic. HTTPS proxy: For web browsing that needs to be secure, especially when encryption is required, such as accessing websites that require authentication. The data encryption it provides helps prevent data from being stolen or tampered with.
5. Flexibility
SOCKS5 Proxy: More flexible, users can optionally configure proxy connections for specific applications such as browsers, FTP clients, online games, etc. It's not limited to web browsing like HTTP proxies and can support a wider range of applications. HTTP proxies: They are usually only used for browsers or web services, and cannot support other types of applications, such as real-time messaging, file transfers, etc. HTTPS proxy: Similar to HTTP proxy, it is mainly used to support HTTPS traffic, and its applicability is limited.
6. Privacy Protection
SOCKS5 proxies: Help protect users' anonymity by hiding their IP addresses, but they don't prevent data breaches or identity theft because they don't encrypt data. HTTP proxy: Because data is not encrypted, HTTP proxies have a weak effect on privacy protection and are easy to be intercepted or monitored by attackers. HTTPS proxy: Provides some privacy protection and protects against man-in-the-middle attacks by encrypting data, but is only effective for HTTPS traffic and cannot protect other types of traffic.
7. Scope of application
SOCKS5 Proxy: Capable of supporting all types of applications and services, especially for tasks that require anonymity and are not limited to web browsing. HTTP/HTTPS proxy: Primarily used to process web traffic, HTTPS proxies require SSL encryption and are suitable for security-critical web browsing activities.
Comparison of SOCKS5 proxies with other proxies
1. P2P/Download
SOCKS5 Proxies: SOCKS5 proxies can effectively hide the user's IP address and are suitable for P2P download activities (such as torrenting, BitTorrent, etc.). While SOCKS5 proxies don't encrypt traffic, they are able to bypass geo-restrictions and reduce monitoring from ISPs. If privacy encryption isn't a priority, SOCKS5 is an excellent choice, especially if speed is required. HTTP proxy: HTTP proxies are generally not suitable for P2P downloads because they only support HTTP and HTTPS traffic and often don't have the ability to bypass network restrictions or hide file transfer activity. As a result, HTTP proxies are not suitable for P2P downloads. HTTPS proxy: While an HTTPS proxy provides security for browsers to encrypt traffic, its role is limited to HTTP/HTTPS requests, making it unsuitable for P2P downloads or other types of traffic.
2. Speed
SOCKS5 proxies: With no encrypted traffic, SOCKS5 proxies typically offer faster connection speeds than other proxies and are suitable for bandwidth-intensive activities such as online gaming, HD video streaming, or large file downloads. Its low latency is ideal for real-time communication and tasks that require high bandwidth. HTTP proxy: An HTTP proxy is usually slower because it primarily handles web traffic and is not optimized. Because HTTP proxies involve additional processing of requests and responses, speeds are often low, especially when dealing with large volumes of traffic. HTTPS proxy: Similar to HTTP proxies, HTTPS proxies handle encrypted traffic, so their speed may also be affected. While it secures HTTPS requests, it's still slower than SOCKS5 proxies, especially for tasks that require high bandwidth.
3. Price
SOCKS5 proxies: SOCKS5 proxies are relatively inexpensive because they do not require data encryption and typically do not require complex client configurations. It's a more cost-effective option for users who are on a budget but need high performance. HTTP proxies: HTTP proxies are generally less expensive, but they also have limited functionality. Its limitations make it unsuitable for handling non-HTTP protocol traffic, but it's a cost-effective option for basic web browsing tasks. HTTPS proxy: An HTTPS proxy is usually slightly more expensive than an HTTP proxy because it needs to support SSL/TLS encryption. However, it's usually priced lower than SOCKS5 proxies and is suitable for those who just need to protect their browsing data.
Using SOCK5 tutorials
To use SOCKS5, you first need to find a reliable SOCKS5 proxy service provider and obtain the necessary proxy information. Here are the basic steps you need to complete:
Choose a reliable SOCKS5 proxy service provider:
- Free Proxies or Free Proxy Lists: While there are free SOCKS5 proxy services available on the web, they are generally not as reliable as paid proxies and can be a security risk. Free proxies are generally shared, have lower bandwidth, and don't guarantee stability and privacy.
- Rapidseedbox: Provides dedicated IPv4 and IPv6 SOCKS5 proxy servers with support for unlimited bandwidth and IP rotation. This service is suitable for purposes such as data scraping, market research, and search engine optimization. They offer 24/7 customer support and a 14-day money-back guarantee.
- Bright Data (formerly Luminati): With over 72 million real residential IPs and data center IPs, it's suitable for users around the world. Bright Data offers global coverage for users who need large-scale data scraping and market research.
- Oxylabs: A leader in residential IP addresses, offering more than 2 million dedicated data center IPs and 100 million residential IPs in approximately 188 countries around the world. Oxylabs also offers a dedicated account manager and session control features.
- Smartproxy: Provides 400,000 US IP addresses and sequential, non-sequential IP options for users who need high-frequency IP switching and large-scale crawling tasks.
Configure the SOCKS5 agent on the device.
Configure SOCKS5 on macOS.
To configure a SOCKS5 proxy server for your default browser in macOS, you need to go to System Preferences > Network > (Select Interface) > Advanced > Proxy.
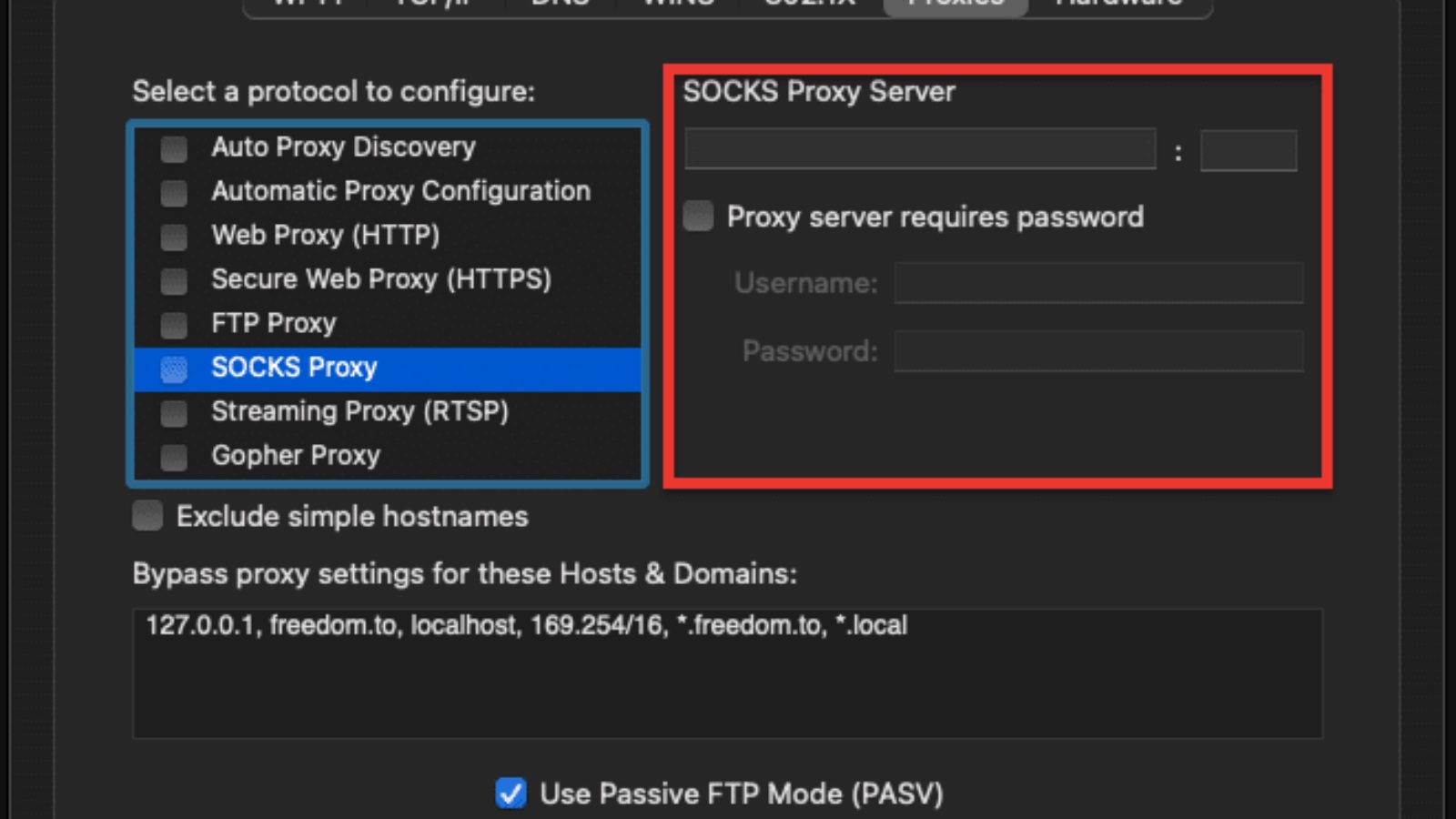
Configure SOCKS5 on Windows.
To configure a SOCKS proxy server on Windows 10, go to Settings > Network and Internet > Proxy.
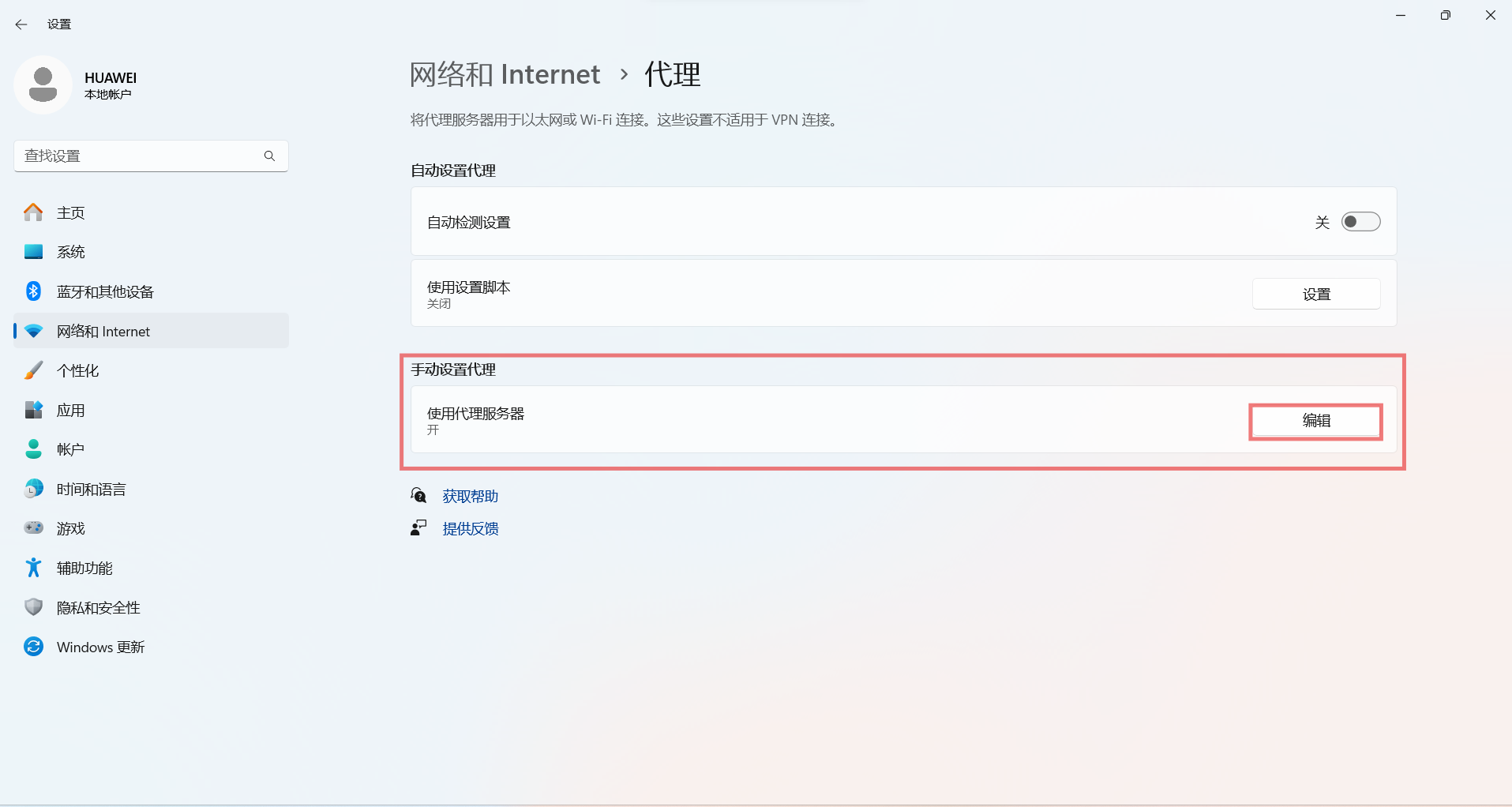
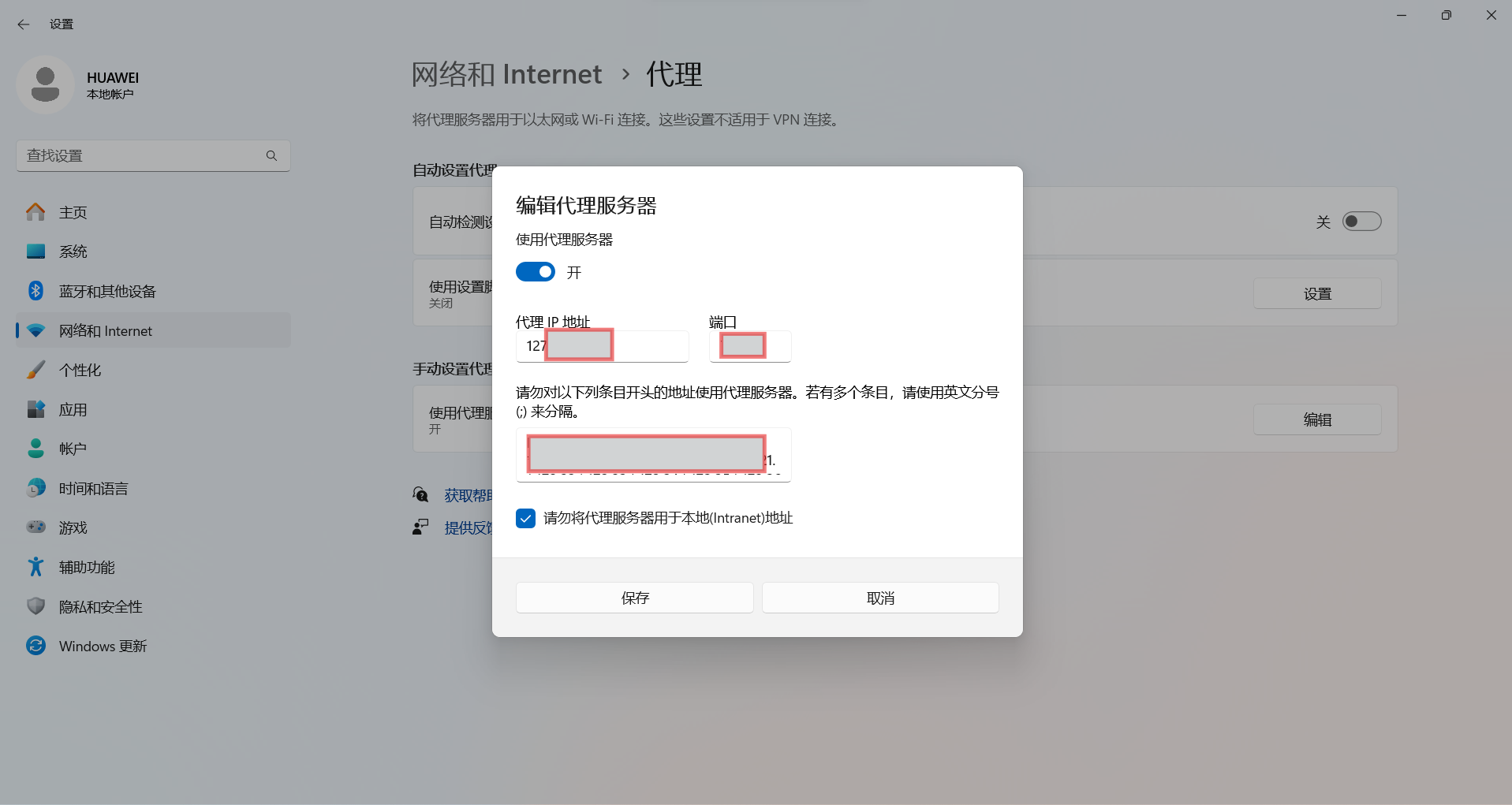
Configure SOCK5 on DICloak
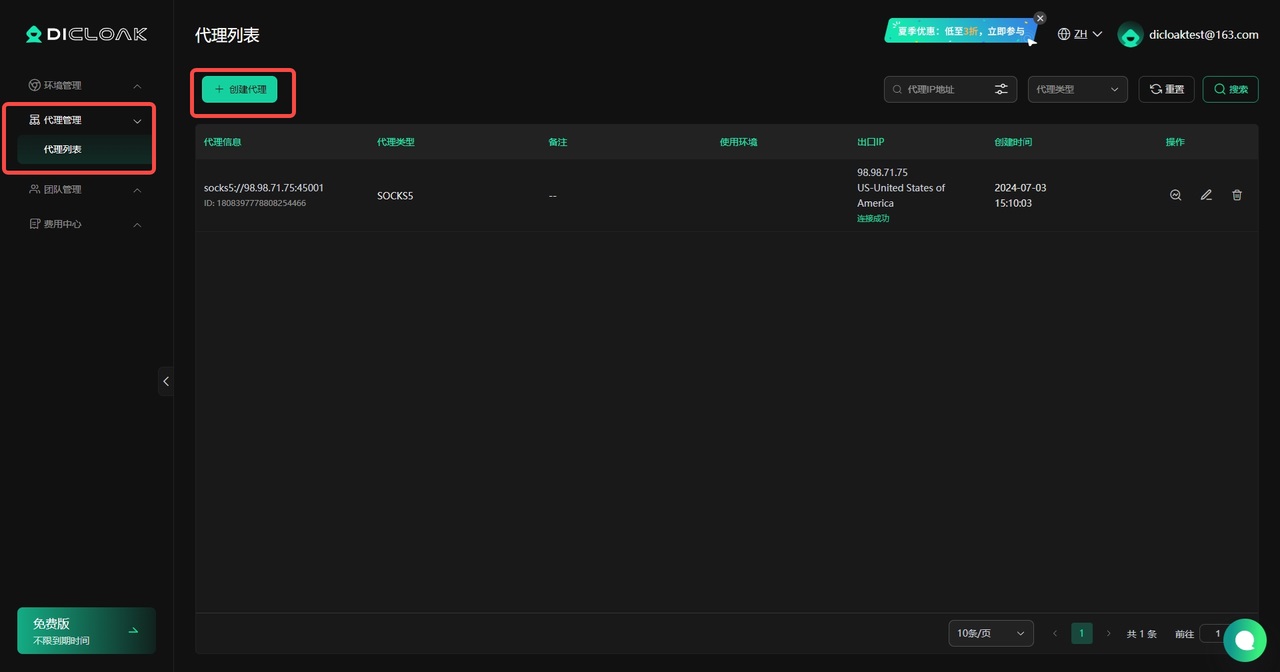
1. Create an agent
Open and log in to the DICloak software, find [Agent Management] in the left navigation bar, enter the [Agent List] page, and click the [Create Agent] button.
2. Fill in the agent information
You select the relevant proxy type based on the proxy information you purchased and complete the proxy information:
- Proxy types: DICloak supports the following proxy types: HTTP, HTTPS, SOCKS5, and IPFLY (dynamic proxy).
- Proxy Host: Fill in the proxy host information you have purchased (Proxy host refers to a proxy server, which is an intermediary device or software located in the network that acts as a transit point between users and the Internet. )
- Proxy Port: Enter the proxy port information that you have purchased (Proxy port refers to the port number that is open for communication on the proxy server.) In network communication, each service or application uses a specific port number to communicate with other devices or services. Proxy ports allow users to connect to the internet through a proxy server and transmit data. )。
- Affiliate Account: Fill in the information of the affiliate account you have purchased.
- Proxy Password: Fill in the proxy password information you have purchased.
- Note: You can supplement the relevant information of the agent for easy management.
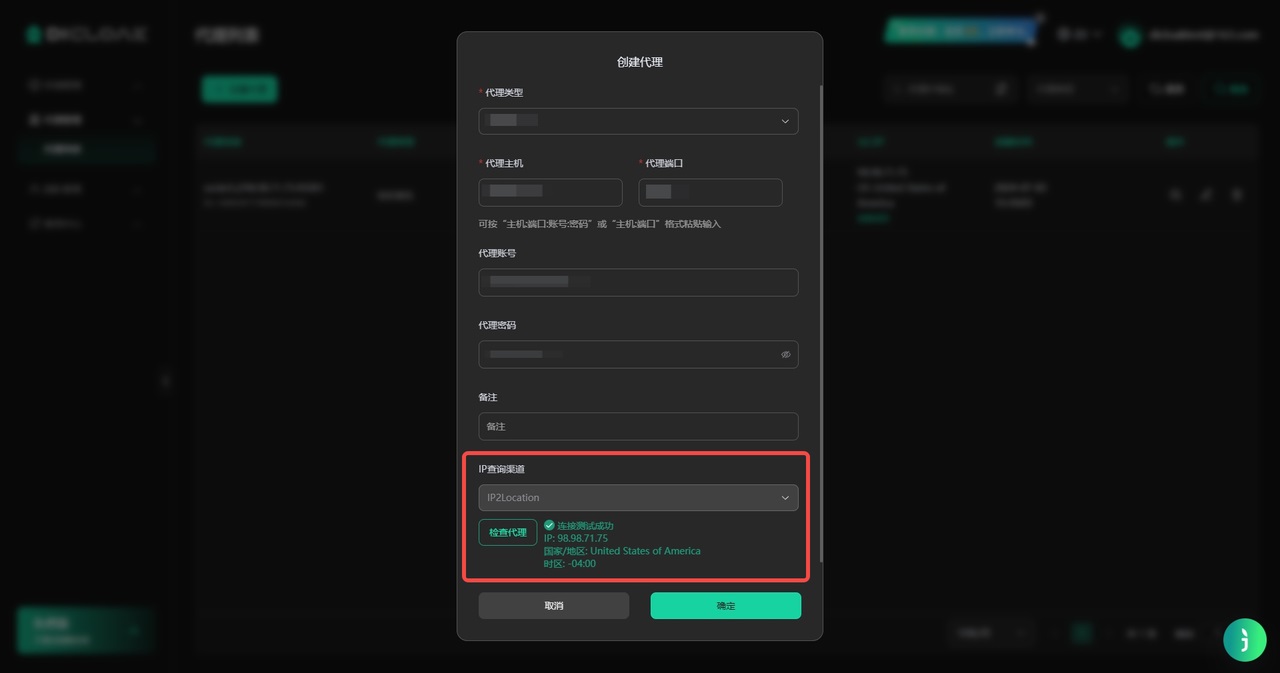
3. Check the proxy
- After filling in the proxy information, you need to click [Check Proxy] to check whether the proxy connection is successful, if the connection is unsuccessful, you need to check whether the proxy information filled in is correct and whether the purchased proxy is available.
4. Confirm the creation of the agent
- You can click the [Confirm] button to complete the proxy creation.
- After the proxy is created, you can return to the Proxy List to view the created proxy information.
Considerations for using SOCKS5 proxies
While it provides users with convenient anonymity and the ability to bypass network restrictions when using SOCKS5 proxies, there are some caveats to know and follow:
- Choose a reliable proxy provider: It is important to choose a reputable SOCKS5 proxy provider. Reliable providers usually guarantee stable connections, high speeds, and excellent customer service. Choose a proxy service provider with good reviews and support to avoid encountering low-quality services or insecure proxies.
- Security Concerns: Unencrypted Traffic: SOCKS5 proxies do not provide encryption by themselves, they only act as an intermediary for traffic forwarding. As a result, when using SOCKS5 proxies, your data can still be exposed to malicious attackers, especially if you're connected to a public network. If you need more security, it's recommended to consider using other encryption techniques to protect your traffic. Combined encryption: Some SOCKS5 proxy services may offer additional security features, such as encryption or authentication support for data, which can reduce security risks. Try to choose a service provider that offers these additional security features.
- Avoid using free proxies: Privacy and security concerns: Free SOCKS5 proxy services often run the risk of privacy breaches, and many free proxies may log your activity or sell your data. Free proxy services often lack a high standard of security, so there is a possibility of malicious use. To avoid potential security risks, it is advisable to opt for a paid SOCKS5 proxy service. Unstable connections: Free proxies often face problems such as unstable connections and insufficient bandwidth, which may affect your experience, especially in scenarios that require high-speed and stable connections (such as gaming, streaming, etc.).
- Comply with the Web Terms of Service: Legality and Compliance: When using SOCKS5 proxies, you need to ensure that you comply with the terms of use and laws and regulations of the websites or services you visit. Some websites and web services may prohibit access to their content through proxies, especially if they involve bypassing geo-restrictions or preventing malicious behavior. When using SOCKS5 proxies, it is important to understand and comply with the relevant policies and regulations to avoid account bans or legal prosecution for violating the rules.
- Avoid abuse: SOCKS5 proxies can help you bypass web restrictions, but misusing proxies for malicious actions such as cyberattacks, illegal data scraping, etc., can lead to your IP being blocked, or legal issues arise. Try to use SOCKS5 proxy services within a legal and ethical framework.
- Ensure the stability and speed of the proxy server: Since SOCKS5 proxies are not encrypted, they are relatively fast, but they can also be affected by the load of the proxy server. Choose a proxy that offers high-performance servers and stable connections, especially if you have heavy traffic needs, such as data scraping or streaming.
frequently asked questions
1. How is a SOCKS5 proxy different from an HTTP proxy?
SOCKS5 proxies support a wider variety of network protocols (e.g., UDP, TCP), while HTTP proxies only support HTTP protocols with more restrictions. SOCKS5 proxies can handle more types of traffic.
2. How do I set up SOCKS5 proxies in my browser?
Go to the settings menu of your browser, find the proxy settings option, and fill in the server address and port number of the SOCKS5 proxy. Different browsers have slightly different settings, please refer to the corresponding help documentation.
3. Will SOCKS5 proxies affect my internet speed?
Yes, when using SOCKS5 proxies, the network speed may be affected to some extent depending on factors such as the quality, bandwidth, and latency of the proxy server.
4. Does SOCKS5 expose my personal information?
SOCKS5 proxies don't encrypt traffic by themselves, so there's a certain risk of privacy breaches. If the proxy service provider is unreliable, it may log your online activity. It is advisable to choose a reputable proxy service provider.
5. Is it possible to access all websites through SOCKS5 proxies?
SOCKS5 proxies can access most websites, but some specific websites or services may take steps to block connections through the proxy. This depends on your site's protection policy.